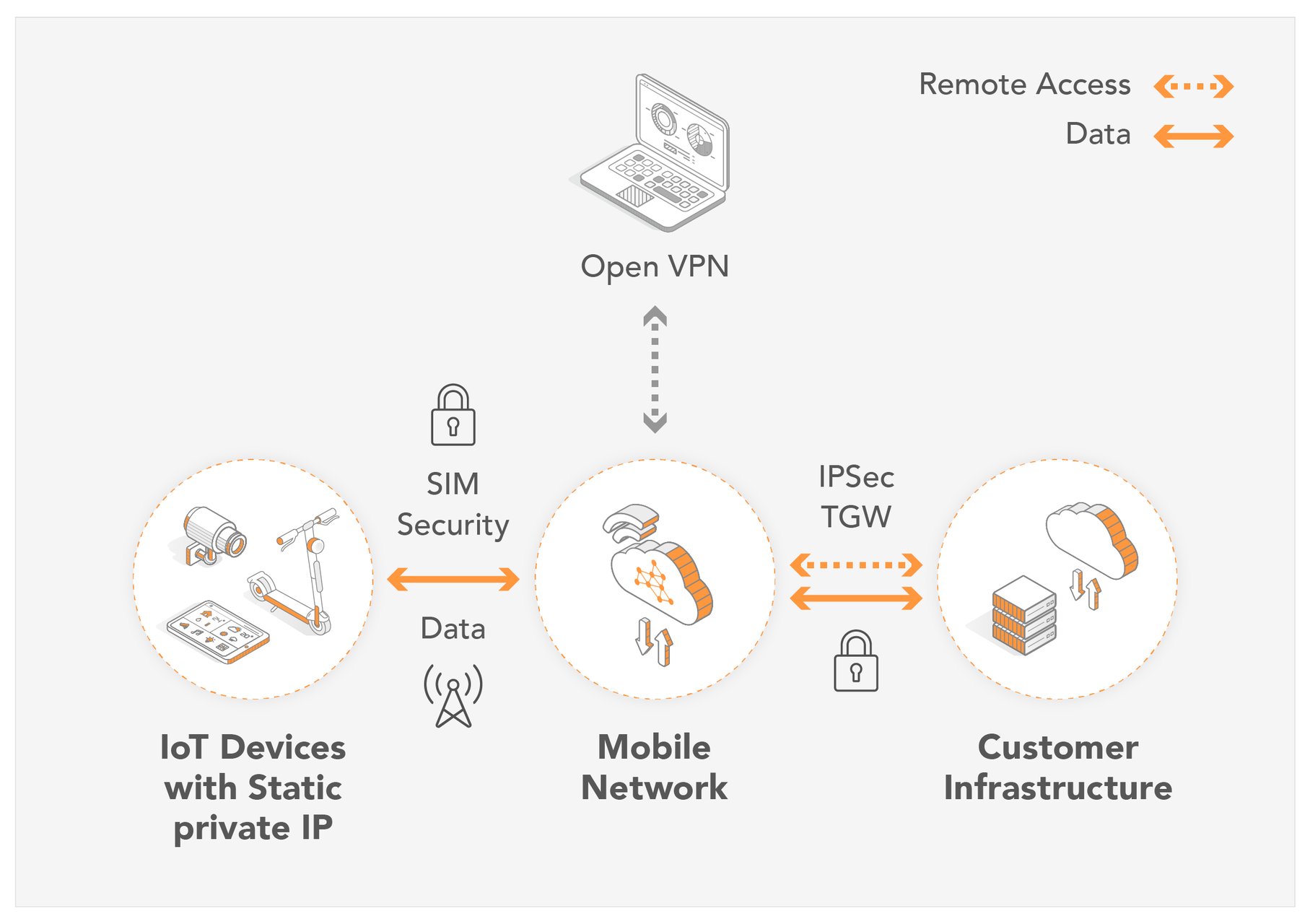
Are you looking for a reliable way to manage IoT devices remotely while ensuring robust security? VNC remote access combined with IoT firewall solutions offers a powerful approach to secure and efficient device management. With the increasing number of IoT devices in homes and businesses, the need for secure remote access has never been more critical. This article delves into the world of VNC remote access, IoT firewalls, and how you can download and implement these tools effectively.
Remote access technology has revolutionized how we interact with devices and networks, especially in the IoT space. From smart homes to industrial automation, VNC remote access provides a seamless way to control devices from anywhere in the world. However, with convenience comes risk, and that’s where IoT firewalls play a crucial role. These firewalls act as a protective barrier, ensuring that your IoT ecosystem remains secure from cyber threats.
In this article, we will explore the fundamentals of VNC remote access, its integration with IoT devices, and the importance of firewalls in securing your network. By the end, you’ll have a clear understanding of how to download and configure these tools to maximize both convenience and security. Let’s dive in!
Read also:Czech Wife Swap 2 Actress A Comprehensive Look Into The Controversial Film
Table of Contents
- What is VNC Remote Access?
- IoT Firewalls Explained
- Benefits of VNC for IoT Management
- How to Download VNC Software
- Setting Up an IoT Firewall
- Securing Remote Access for IoT Devices
- Best Practices for VNC and IoT Firewall
- Common Challenges and Solutions
- Case Study: Successful VNC and IoT Firewall Implementation
- Conclusion
What is VNC Remote Access?
VNC, or Virtual Network Computing, is a graphical desktop-sharing system that allows you to remotely control another computer. It transmits keyboard and mouse events from one device to another, enabling you to interact with the remote device as if you were physically present.
VNC remote access is particularly valuable for IoT environments, where devices are often distributed across different locations. With VNC, administrators can troubleshoot issues, update software, and monitor device performance without needing physical access.
How VNC Works
VNC operates on a client-server model. The server component runs on the device you want to control, while the client is installed on the device you’ll use to initiate the connection. Once connected, the client displays the server’s desktop environment in a window.
- Server: Installed on the remote device.
- Client: Installed on the controlling device.
- Protocol: Uses the RFB (Remote Frame Buffer) protocol for communication.
IoT Firewalls Explained
An IoT firewall is a specialized security solution designed to protect IoT devices from unauthorized access and cyber threats. Unlike traditional firewalls, IoT firewalls are optimized for the unique characteristics of IoT networks, such as low bandwidth and diverse device types.
IoT firewalls monitor incoming and outgoing traffic, block malicious activities, and enforce security policies. They are essential for safeguarding sensitive data and ensuring the smooth operation of IoT ecosystems.
Key Features of IoT Firewalls
- Traffic Filtering: Blocks unauthorized access attempts.
- Intrusion Detection: Identifies suspicious activities in real-time.
- Device Authentication: Ensures only authorized devices can connect.
Benefits of VNC for IoT Management
VNC remote access offers several advantages for managing IoT devices, making it a popular choice for businesses and individuals alike. Below are some of the key benefits:
Read also:Kpop Vote Everything You Need To Know About Voting For Your Favorite Kpop Stars
- Convenience: Access IoT devices from anywhere in the world.
- Cost-Effectiveness: Reduces the need for on-site maintenance.
- Real-Time Monitoring: Provides instant insights into device performance.
Use Cases
VNC is widely used in various industries, including healthcare, manufacturing, and smart homes. For example, in healthcare, VNC enables remote monitoring of medical devices, ensuring timely interventions.
How to Download VNC Software
Downloading VNC software is a straightforward process, but it’s essential to choose a reputable provider to ensure security and reliability. Here’s a step-by-step guide:
- Step 1: Visit the official website of a trusted VNC provider, such as RealVNC or TightVNC.
- Step 2: Navigate to the download section and select the version compatible with your operating system.
- Step 3: Follow the installation instructions provided on the website.
- Step 4: Configure the software according to your requirements.
Recommended VNC Providers
- RealVNC: Known for its robust security features.
- TightVNC: Offers lightweight and efficient performance.
- UltraVNC: Provides advanced customization options.
Setting Up an IoT Firewall
Setting up an IoT firewall involves several steps to ensure it effectively protects your network. Below is a general guide:
- Step 1: Assess your IoT network to identify potential vulnerabilities.
- Step 2: Choose a firewall solution tailored to IoT environments.
- Step 3: Install the firewall software or hardware on your network.
- Step 4: Configure security policies to block unauthorized access.
Tips for Effective Firewall Configuration
- Regularly update firewall rules to adapt to new threats.
- Enable logging to monitor traffic patterns.
- Conduct periodic security audits to identify gaps.
Securing Remote Access for IoT Devices
While VNC remote access offers convenience, it’s crucial to implement security measures to protect your IoT devices from cyber threats. Below are some best practices:
- Use strong passwords and enable two-factor authentication (2FA).
- Encrypt all data transmitted between devices.
- Restrict access to trusted IP addresses only.
Encryption Protocols
Encryption is a key component of securing remote access. Protocols like SSL/TLS ensure that data remains confidential during transmission.
Best Practices for VNC and IoT Firewall
To maximize the benefits of VNC remote access and IoT firewalls, consider the following best practices:
- Regularly update VNC software to patch vulnerabilities.
- Integrate firewalls with other security tools for comprehensive protection.
- Educate users about safe remote access practices.
Combining VNC and IoT Firewalls
Integrating VNC with IoT firewalls creates a robust security framework. Firewalls can monitor VNC traffic, ensuring that only legitimate connections are allowed.
Common Challenges and Solutions
Implementing VNC remote access and IoT firewalls can present challenges, such as compatibility issues and network latency. Here’s how to address them:
- Challenge: Compatibility issues with IoT devices. Solution: Use VNC software that supports a wide range of devices.
- Challenge: Network latency affecting performance. Solution: Optimize network settings and use high-speed connections.
Overcoming Security Concerns
Security concerns can be mitigated by implementing strong encryption, regular updates, and user training.
Case Study: Successful VNC and IoT Firewall Implementation
A leading manufacturing company successfully implemented VNC remote access and IoT firewalls to manage its smart factory. By integrating these tools, the company achieved:
- Reduced downtime through real-time monitoring.
- Enhanced security with IoT firewalls blocking unauthorized access.
- Improved operational efficiency with remote troubleshooting.
Key Takeaways
This case study highlights the importance of combining VNC and IoT firewalls for secure and efficient IoT management.
Conclusion
VNC remote access and IoT firewalls are indispensable tools for managing IoT devices securely and efficiently. By downloading and configuring these tools correctly, you can enjoy the benefits of remote access while safeguarding your network from cyber threats.
We encourage you to explore the solutions mentioned in this article and implement them in your IoT ecosystem. If you found this guide helpful, please share it with others and leave a comment with your thoughts or questions. For more insights, check out our other articles on IoT security and remote management.