Are you looking for a reliable way to securely access your Raspberry Pi remotely? In today’s interconnected world, remote access to devices like the Raspberry Pi has become essential for developers, hobbyists, and professionals alike. However, ensuring that this access is secure is equally important to protect your data and device from potential threats. This article will guide you through the best practices, tools, and techniques to establish secure remote access to your Raspberry Pi while adhering to principles of safety and efficiency.
Remote access to a Raspberry Pi can open up a world of possibilities, from managing IoT devices to running server applications. However, without proper security measures, your Raspberry Pi could become vulnerable to cyberattacks. That’s why it’s crucial to follow expert-recommended steps to safeguard your device. In this article, we will explore the tools, protocols, and configurations needed to ensure secure remote access.
Whether you’re a beginner or an experienced user, this guide is designed to provide actionable insights and detailed instructions. By the end of this article, you’ll have a clear understanding of how to configure secure remote access to your Raspberry Pi and protect it from unauthorized access. Let’s dive into the details and get started!
Read also:Unveiling The Mysteries Of September 15 Zodiac A Comprehensive Guide
Table of Contents
- Introduction to Secure Remote Access
- Why Secure Remote Access Matters
- Essential Tools for Remote Access
- Step-by-Step Guide to Setting Up SSH
- Using VPN for Secure Access
- Securing Your Raspberry Pi with a Firewall
- Remote Desktop Access with VNC
- Best Practices for Secure Remote Access
- Troubleshooting Common Issues
- Conclusion and Next Steps
Introduction to Secure Remote Access
Remote access allows you to control and manage your Raspberry Pi from anywhere in the world. This capability is particularly useful for IoT projects, home automation, and server management. However, remote access also introduces potential security risks, such as unauthorized access and data breaches. Understanding the basics of secure remote access is the first step toward protecting your Raspberry Pi.
Secure remote access involves using encrypted communication channels, strong authentication methods, and robust security configurations. These measures ensure that only authorized users can access your device while keeping sensitive data safe from prying eyes. In the following sections, we’ll explore the tools and techniques that can help you achieve this level of security.
Why Secure Remote Access Matters
Secure remote access is not just a convenience—it’s a necessity. Without proper security measures, your Raspberry Pi could become a target for hackers. Cybercriminals often exploit weak configurations and outdated software to gain unauthorized access to devices. This can lead to data theft, malware infections, or even the hijacking of your Raspberry Pi for malicious purposes.
For devices like the Raspberry Pi, which are often used in IoT applications, the stakes are even higher. A compromised Raspberry Pi could provide attackers with access to your entire network or sensitive personal information. By implementing secure remote access protocols, you can mitigate these risks and ensure that your device remains safe and functional.
Essential Tools for Remote Access
To establish secure remote access to your Raspberry Pi, you’ll need to use a combination of tools and protocols. Below are some of the most essential tools you should consider:
- SSH (Secure Shell): A protocol that allows secure command-line access to your Raspberry Pi.
- VPN (Virtual Private Network): Encrypts your internet connection and provides a secure tunnel for remote access.
- VNC (Virtual Network Computing): Enables remote desktop access to your Raspberry Pi’s graphical interface.
- UFW (Uncomplicated Firewall): A user-friendly tool for managing firewall rules on your Raspberry Pi.
Step-by-Step Guide to Setting Up SSH
SSH is one of the most common and secure ways to access your Raspberry Pi remotely. Below is a detailed guide to setting up SSH on your device.
Read also:How Much Did Jim Parsons Make Per Episode Of Young Sheldon A Comprehensive Breakdown
Installing SSH on Raspberry Pi
By default, SSH is disabled on most Raspberry Pi operating systems. To enable it, follow these steps:
- Open the terminal on your Raspberry Pi.
- Type the following command:
sudo raspi-config. - Navigate to “Interfacing Options” and select “SSH.”
- Choose “Yes” to enable SSH and exit the configuration tool.
Configuring SSH for Security
Once SSH is enabled, it’s important to configure it for maximum security:
- Change the default username and password to something more secure.
- Disable password authentication and use SSH keys for login.
- Restrict SSH access to specific IP addresses using firewall rules.
Using VPN for Secure Access
A VPN provides an additional layer of security by encrypting your connection and masking your IP address. Setting up a VPN for your Raspberry Pi involves installing a VPN server on your device or using a third-party service. This ensures that all communication between your Raspberry Pi and remote devices is encrypted and secure.
Securing Your Raspberry Pi with a Firewall
A firewall is a critical component of any secure remote access setup. The UFW tool is a simple yet effective way to manage firewall rules on your Raspberry Pi. By allowing only necessary ports and blocking unauthorized access, you can significantly reduce the risk of cyberattacks.
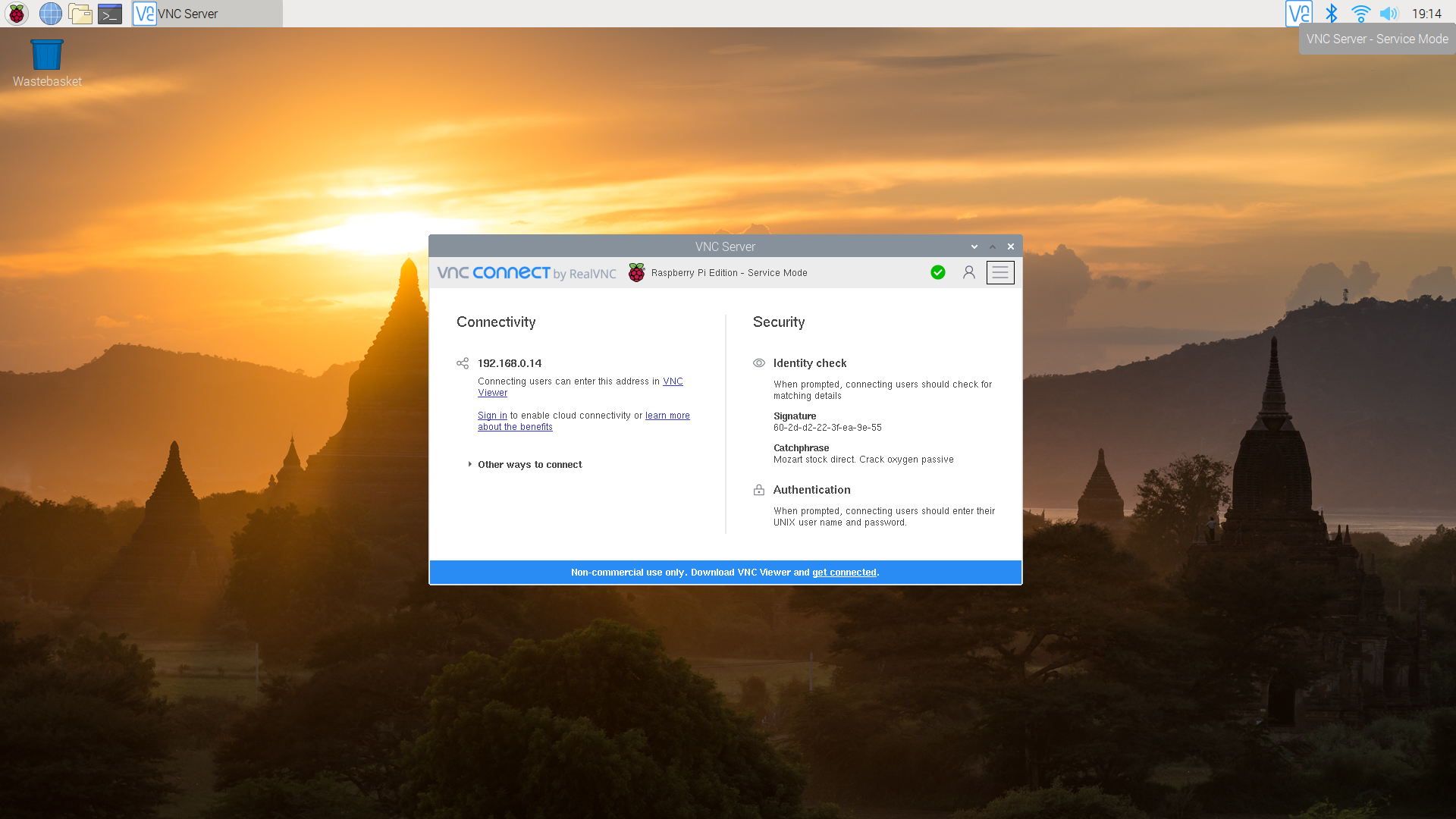
Remote Desktop Access with VNC
If you prefer a graphical interface, VNC is an excellent option for remote access. It allows you to control your Raspberry Pi’s desktop environment from another device. To set up VNC, install the VNC server on your Raspberry Pi and connect using a VNC client on your remote device.
Best Practices for Secure Remote Access
Here are some additional tips to enhance the security of your remote access setup:
- Regularly update your Raspberry Pi’s operating system and software.
- Use strong, unique passwords for all accounts.
- Monitor your device for suspicious activity using log files.
- Limit the number of users with remote access privileges.
Troubleshooting Common Issues
Despite your best efforts, you may encounter issues with remote access. Common problems include connection timeouts, authentication errors, and firewall blockages. To resolve these issues, check your network settings, verify your credentials, and ensure that all necessary ports are open.
Conclusion and Next Steps
Secure remote access to your Raspberry Pi is essential for protecting your device and data. By following the steps outlined in this guide, you can establish a secure and reliable connection while minimizing the risk of cyberattacks. Remember to regularly update your security configurations and stay informed about emerging threats.
We encourage you to share your thoughts in the comments below or reach out if you have any questions. Additionally, explore our other articles for more tips on Raspberry Pi projects and security best practices. Together, we can create a safer and more connected world!