Remote login device behind firewall is a crucial topic for anyone managing IT infrastructure or working with remote devices. In today’s interconnected world, accessing devices behind a firewall is not just a convenience but often a necessity. Whether you're an IT administrator, a remote worker, or a tech enthusiast, understanding how to securely and efficiently log into devices behind a firewall can save time and resources while maintaining security.
Firewalls are designed to protect networks by controlling incoming and outgoing traffic based on predetermined security rules. While they play a vital role in safeguarding sensitive data, they can also create barriers for legitimate remote access. This article will explore various methods and technologies that allow you to bypass these barriers safely and effectively.
By the end of this guide, you will have a comprehensive understanding of remote login techniques, security considerations, and best practices for accessing devices behind firewalls. Let's dive into the details and uncover the most effective strategies for remote device access.
Read also:Who Is Bruno Mars Dating Discover His Love Life Relationship History And More
Table of Contents
Understanding Firewalls
A firewall is a network security device that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Firewalls act as a barrier between a trusted network and untrusted networks, such as the internet. They are essential for protecting sensitive data and preventing unauthorized access to devices and networks.
Firewalls can be hardware-based, software-based, or a combination of both. They operate by examining packets of data and determining whether to allow or block them based on predefined rules. These rules can be based on IP addresses, protocols, ports, or specific applications.
While firewalls are critical for network security, they can sometimes hinder legitimate remote access. Understanding how firewalls work is the first step in finding effective solutions for remote login behind firewalls.
The Importance of Remote Access
In today's fast-paced and interconnected world, remote access is more important than ever. Businesses rely on remote access to manage IT infrastructure, troubleshoot issues, and ensure business continuity. Remote workers need access to company resources to perform their jobs effectively.
Remote access allows IT administrators to manage devices and networks from anywhere in the world. This capability is particularly valuable for organizations with multiple locations or remote employees. It enables quick response to issues, reduces downtime, and improves overall efficiency.
However, remote access must be balanced with security. Unauthorized access to devices behind firewalls can lead to data breaches, malware infections, and other security risks. Therefore, it's essential to implement secure remote access methods that protect sensitive data while allowing legitimate access.
Read also:Oink Heart Movies A Comprehensive Guide To The Wholesome Trend Taking Over Cinema
Methods for Remote Login Behind Firewalls
1. Virtual Private Networks (VPNs)
VPNs are one of the most common methods for remote login behind firewalls. A VPN creates a secure, encrypted connection between a remote device and a private network, allowing users to bypass firewall restrictions.
2. SSH Tunneling
SSH tunneling involves creating an encrypted connection between a local device and a remote server using the Secure Shell (SSH) protocol. This method allows users to securely access devices behind firewalls by forwarding traffic through the tunnel.
3. Port Forwarding
Port forwarding involves configuring a router or firewall to redirect incoming traffic on a specific port to a device on the internal network. This method can be used to allow remote access to devices behind firewalls.
4. Cloud-Based Remote Access
Cloud-based remote access solutions provide a secure and scalable way to access devices behind firewalls. These solutions typically involve installing an agent on the target device and accessing it through a web-based interface.
VPN Solutions
Virtual Private Networks (VPNs) are widely used for remote access to devices behind firewalls. A VPN creates a secure, encrypted tunnel between a remote device and a private network, allowing users to bypass firewall restrictions.
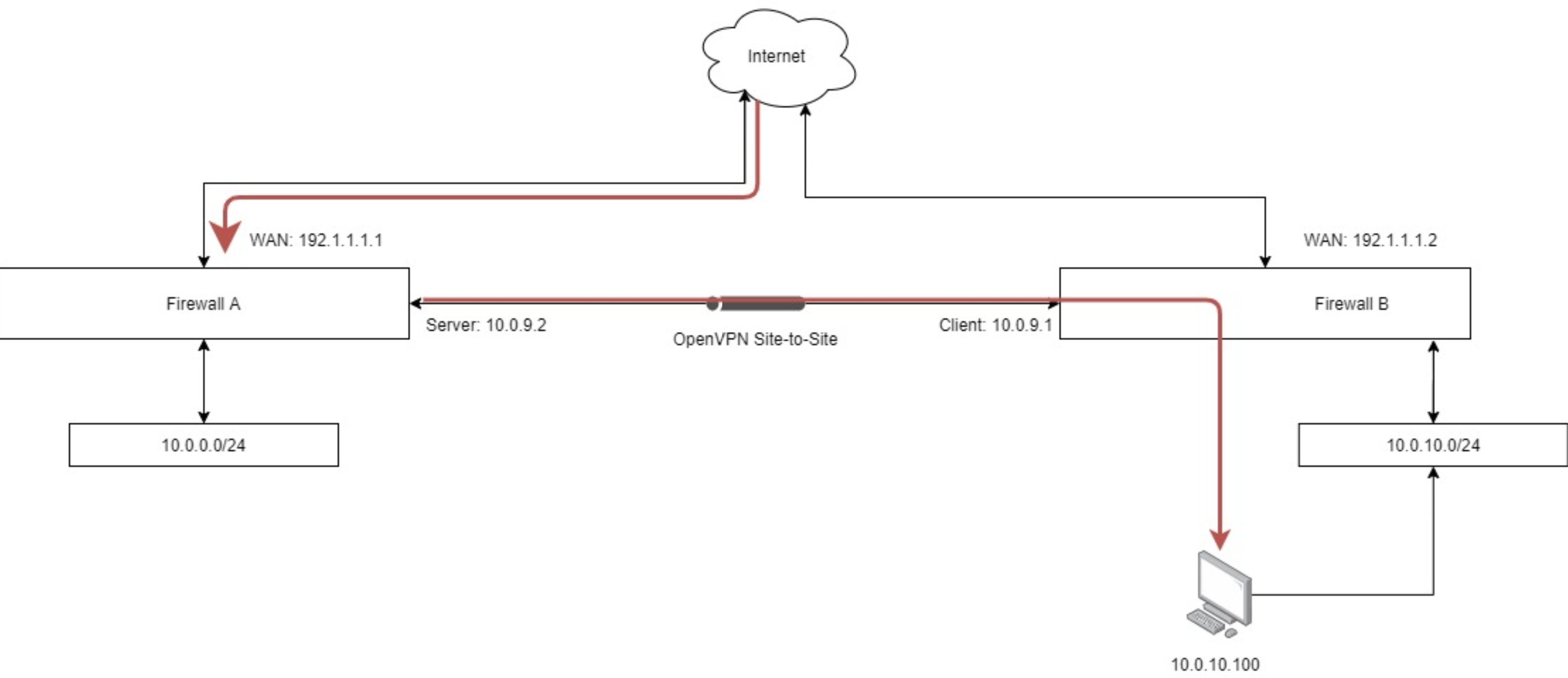
There are two main types of VPNs: remote access VPNs and site-to-site VPNs. Remote access VPNs are used by individual users to connect to a private network from a remote location. Site-to-site VPNs connect entire networks to each other, allowing devices on different networks to communicate securely.
VPNs offer several advantages, including enhanced security, privacy, and flexibility. However, they also have some drawbacks, such as potential performance issues and the need for proper configuration to ensure security.
SSH Tunneling
SSH tunneling is a method of securely accessing devices behind firewalls by creating an encrypted connection between a local device and a remote server. This method is particularly useful for accessing services that are not directly accessible from the internet.
To set up an SSH tunnel, users need to have SSH access to a server that is accessible from both the local and remote networks. Once the tunnel is established, traffic can be forwarded through the tunnel to access devices behind the firewall.
SSH tunneling offers several benefits, including strong encryption, flexibility, and ease of use. However, it requires technical knowledge to set up and configure properly.
Port Forwarding
Port forwarding involves configuring a router or firewall to redirect incoming traffic on a specific port to a device on the internal network. This method can be used to allow remote access to devices behind firewalls.
To set up port forwarding, users need to configure the router or firewall to forward traffic on a specific port to the IP address and port of the target device. This allows external devices to connect to the target device using the router's public IP address and the forwarded port.
Port forwarding is relatively easy to set up but can pose security risks if not configured properly. It's essential to use strong passwords and limit access to trusted IP addresses to minimize risks.
Cloud-Based Remote Access
Cloud-based remote access solutions provide a secure and scalable way to access devices behind firewalls. These solutions typically involve installing an agent on the target device and accessing it through a web-based interface.
Some popular cloud-based remote access solutions include TeamViewer, AnyDesk, and Chrome Remote Desktop. These tools offer features such as file transfer, remote printing, and multi-platform support.
Cloud-based remote access solutions offer several advantages, including ease of use, scalability, and security. However, they may require a subscription fee and rely on third-party services for access.
Security Considerations
When accessing devices behind firewalls, security should be a top priority. Unauthorized access can lead to data breaches, malware infections, and other security risks.
To ensure secure remote access, users should implement strong authentication methods, such as multi-factor authentication (MFA). It's also essential to use encryption to protect data in transit and ensure that all software and systems are up to date with the latest security patches.
Additionally, users should limit access to trusted IP addresses and monitor remote access activity for suspicious behavior. Regular security audits and penetration testing can help identify and address potential vulnerabilities.
Tools and Software for Remote Access
1. TeamViewer
TeamViewer is a popular remote access tool that allows users to connect to devices behind firewalls securely. It offers features such as file transfer, remote printing, and multi-platform support.
2. AnyDesk
AnyDesk is another widely used remote access solution that provides fast and secure connections. It offers features such as high-performance connections, file transfer, and remote printing.
3. Chrome Remote Desktop
Chrome Remote Desktop is a free remote access tool provided by Google. It allows users to access devices remotely through a web browser and offers features such as multi-platform support and easy setup.
Best Practices for Remote Login Behind Firewalls
To ensure secure and efficient remote access to devices behind firewalls, it's essential to follow best practices. These include implementing strong authentication methods, using encryption, and regularly updating software and systems.
Users should also limit access to trusted IP addresses and monitor remote access activity for suspicious behavior. Regular security audits and penetration testing can help identify and address potential vulnerabilities.
Additionally, it's crucial to educate users on security best practices and provide training on how to use remote access tools safely and effectively.
Conclusion
Accessing remote login device behind firewall is a critical skill for IT administrators, remote workers, and tech enthusiasts. This guide has explored various methods and technologies that allow you to bypass firewall restrictions safely and effectively.
By understanding how firewalls work and implementing secure remote access methods, you can ensure that your devices and networks remain protected while allowing legitimate access. Whether you choose to use VPNs, SSH tunneling, port forwarding, or cloud-based solutions, it's essential to prioritize security and follow best practices.
We hope this article has provided valuable insights and practical solutions for remote login behind firewalls. If you found this guide helpful, please consider sharing it with others or leaving a comment below. For more information on related topics, feel free to explore our other articles.